Navigating the intricacies of the Payment Card Industry Data Security Standard (PCI-DSS) requirements for storing cardholder data can seem daunting. This article serves as a comprehensive guide, aiming to demystify the process by breaking down the essential aspects you need to consider when storing such sensitive information. It’s designed to support your efforts in safeguarding cardholder data, thus reinforcing trust between your business and its customers, whilst maintaining compliance.
This image is property of www.pcidssguide.com.
Overview of PCI-DSS
In today’s data-driven business landscape, protecting financial and personal information is of paramount importance. One of the most critical areas of data protection is the safeguarding of credit and debit card details which is where the Payment Card Industry Data Security Standard (PCI-DSS) comes in.
Definition and Purpose
PCI-DSS is a globally recognized set of protocols designed to ensure all companies and organizations that deal with cardholder information maintain a secure environment. The primary purpose of these standards is to lower the likelihood of card data being misused, either through theft, fraud, hacking, or other data breaches.
History of the PCI-DSS Standards
PCI-DSS was first established in 2004 by a consortium including American Express, JCB International, Discover Financial Services, Visa Inc., and MasterCard. The objective was to create unified standards to enhance cardholder data security, thereby decreasing the potential for monetary losses resulting from data breaches. Since then, the standards have gone through various updates to take into account changes in technology and potential threats.
Key stakeholders: Merchants, Providers, and Customers
In terms of stakeholders, anyone who transacts with cardholder data can be considered a stakeholder. This includes merchants who accept credit or debit cards, payment service providers who process transactions, and customers who use their cards to make purchases. All these stakeholders need to be confident that cardholder information is being appropriately protected and managed.
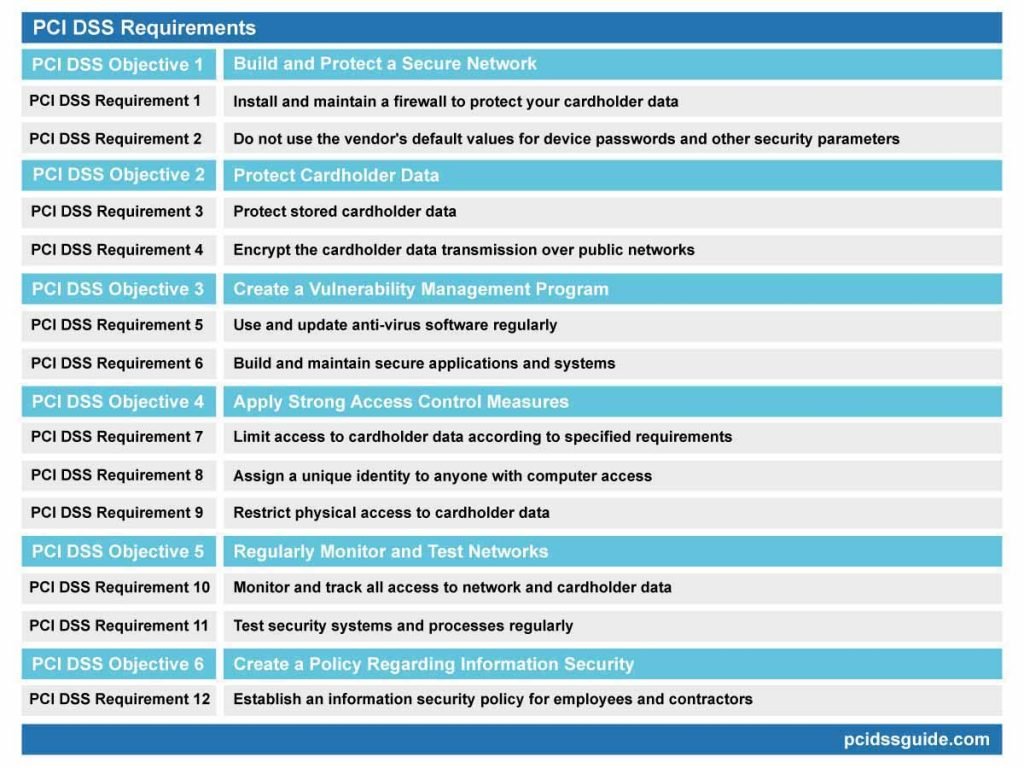
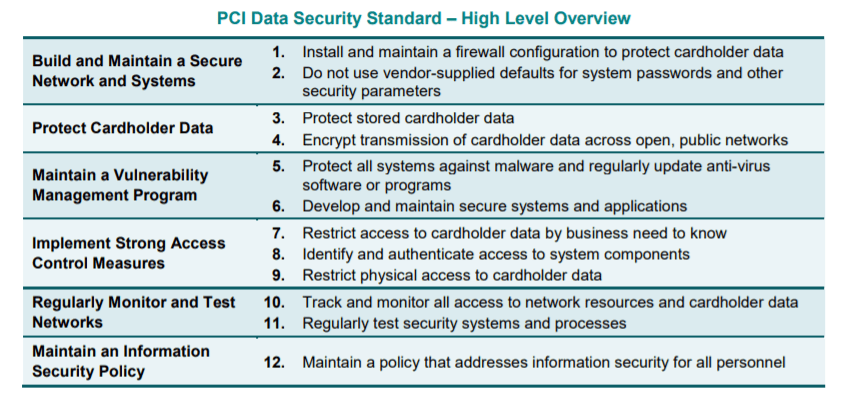
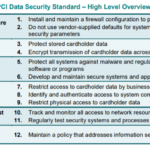
Key Principles and Requirements of PCI-DSS
Understanding the principles and requirements of PCI-DSS is vital for effectively integrating them into your data security systems.
Understanding the Six Basic Principles
The framework of PCI-DSS revolves around six basic principles:
- Building and maintaining a secure network,
- Protecting cardholder data,
- Maintaining a vulnerability management program,
- Implementing robust access control measures,
- Regularly monitoring and testing networks,
- Maintaining an information security policy.
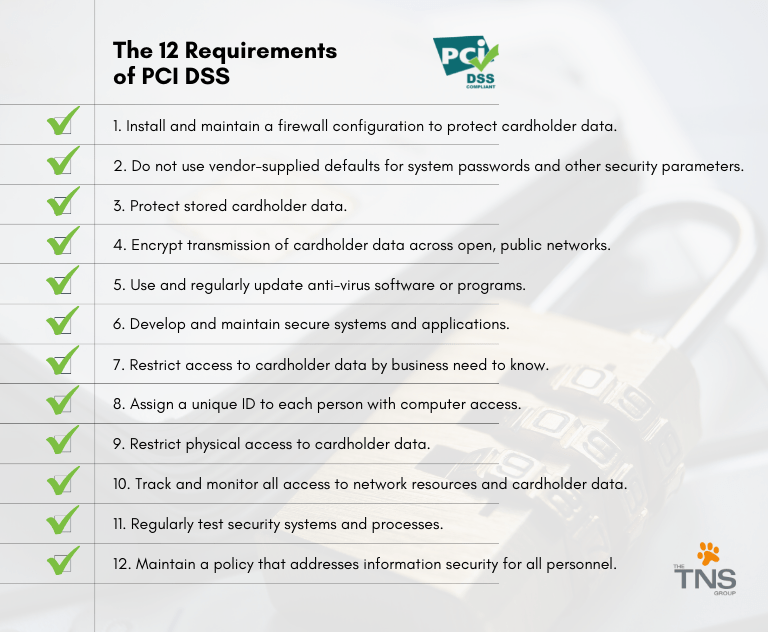
Explanation of 12 Key PCI-DSS requirements
These principles break down into twelve more specific requirements, each aimed at safeguarding cardholder data at various stages in the transaction process. These requirements range from maintaining a secure network to monitoring and controlling access to cardholder data.
Scope of Application of PCI-DSS’s Requirements
Any entity involved in payment card processing, including merchants, processors, acquirers, issuers, and service providers must comply with PCI-DSS requirements. Even organizations that don’t process card payments but store or transmit cardholder data fall within the scope.
Understanding Cardholder Data
Understanding the nature and types of cardholder data is crucial to managing its security properly.
Definition of Cardholder Data
Cardholder data refers to any personally identifiable information (PII) associated with a cardholder. This could include the cardholder’s name, card number (or PAN – Primary Account Number), expiration date, and service code.
Different Types of Cardholder Data
Cardholder data can be classified into two categories: Cardholder Data (CHD) and Sensitive Authentication Data (SAD). CHD includes the cardholder’s name, PAN, and expiration date. SAD involves data used to authenticate transactions such as PINs, CVV, magnetic stripe data, and more.
How Cardholder Data is used
Cardholder data is used in all stages of card processing, including authorization, authentication, transaction processing, and payment settlement. It is vital to protect this data throughout the entire transaction lifecycle to prevent fraudulent activity and potential breaches.
PCI-DSS’s Requirements for Storing Cardholder Data
PCI-DSS outlines several specific requirements for protecting stored cardholder data.
Requirement 3: Protect Stored Cardholder Data
This requirement stipulates that cardholder data needs to be protected at rest. This can be achieved through techniques like encryption, tokenization, truncation, and other forms of data obfuscation.
Understanding Sensitive Authentication Data
Sensitive Authentication Data (SAD) refers to security-related information used to authenticate cardholders. This data should never be stored post-authorization and must be protected when stored temporarily for pre-authorization.
Storage Limitations and Retention Policy
PCI-DSS mandates that cardholder data should only be stored if it’s necessary for business, legal, or regulatory purposes. Moreover, a data retention policy should be implemented to ensure that stored data is deleted once it’s no longer needed.

This image is property of info.varonis.com.
Common Misconceptions about Storing Cardholder Data
Understanding and debunking common misconceptions about storing cardholder data can prevent costly mistakes.
Assuming all data storage needs encryption
While encryption is a fundamental security measure, not all stored data needs to be encrypted. PCI-DSS only requires the encryption of Sensitive Authentication Data and PAN (Primary Account Number).
Misunderstanding around retaining CVV/CSC codes
Another misconception is that businesses can store card security codes (CVV/CSC). However, businesses are prohibited from storing sensitive authentication data, including card security codes, after authorization, even if encrypted.
Confusions about temporary data storage
Another misunderstanding pertains to temporary data storage. While PCI-DSS allows temporary storage of cardholder data under specific conditions, such data must be protected and deleted in a timely manner.
Implementing PCI-DSS Compliant Data Storage
Adopting PCI-DSS compliant data storage practices is a key step toward ensuring the security of your customers’ cardholder data.
Evaluating Current Data Storage Practice
The first step towards implementing PCI-DSS compliant data storage is to evaluate your current practices. Determine what kind of cardholder data you’re storing, how it’s being stored, and whether you need to retain the data or not.
Choosing PCI-DSS Compliant Storage Solutions
Once evaluated, choose PCI-DSS compliant storage solutions that fit your business’s needs. Options can include on-site data storage or cloud-based solutions, each with its own set of considerations regarding cost, security, scalability, and data accessibility.
Addressing Challenges in Data Storage Implementation
Implementing data storage changes can pose challenges, from resistance among staff to budget constraints. Communication, education, careful planning, and incremental changes can address these challenges effectively.
This image is property of www.fa.ufl.edu.
Regular Monitoring and Testing
Regular testing and monitoring are critical elements of the PCI-DSS standards, ensuring ongoing compliance and data security.
Requirement 10: Regularly Monitor and Test Networks
PCI-DSS Requirement 10 expects businesses to establish a process for regularly testing security systems and processes. This includes continuous monitoring of network traffic, regular vulnerability scans, and periodic penetration testing.
Importance of Logging and Network Testing
Logging and Network testing can help identify suspicious activities or vulnerabilities early on, thereby minimizing the risk of a data breach.
Mitigation Strategies for Detected Threats
Upon detecting threats, immediate mitigation strategies should be implemented. These can include patching identified vulnerabilities, tightening network security controls, and initiating incident response processes.
Ensuring Compliance through Policies and Procedures
Maintaining PCI-DSS compliance is not only about technical controls. It also heavily relies on adopting the right policies and procedures.
Requirement 12: Maintain a Policy that Addresses Information Security
PCI-DSS Requirement 12 mandates organizations to establish, publish, and maintain a comprehensive information security policy.
Establishing and Enforcing Data Security Policies
Data security policies should clearly outline the organization’s commitment to safeguarding cardholder data. This should be accompanied by a strong enforcement mechanism.
Continuous Training to Maintain Compliance
Regular training of staff is also crucial to maintain compliance. Updated knowledge about policies, procedures, and potential threats can drastically decrease vulnerability.
This image is property of thetnsgroup.com.
The Risk of Non-compliance
Non-compliance not only risks hefty financial penalties but can also cause long-lasting reputational harm.
Penalties and Consequences of Non-compliance
The penalties for non-compliance can range from hefty fines, termination of card acceptance agreements, credibility loss or even bankruptcy in severe cases.
Impact on Business Reputation
A major data breach resulting from non-compliance can severely damage a business’s reputation, leading to loss of customers and declining sales.
Case Studies of Non-compliance
Numerous case studies highlight the severe consequences of non-compliance, reinforcing the necessity of adhering to PCI-DSS standards.
Reviewing and Updating Compliance Strategies
Compliance isn’t a one-time event but an ongoing commitment to maintaining the highest level of data protection.
The Dynamic Nature of Data Security Environment
As the field of data security continually evolves, businesses need to regularly review and update their compliance strategies to address new threats and vulnerabilities.
Need for Ongoing Compliance Review
An ongoing compliance review helps ensure that every step of the card transaction process remains secure and adheres to PCI-DSS standards.
Strategies for Staying Updated With New Standards and Practices
Staying updated with the most recent security standards and practices requires regular training and education about the latest changes to PCI-DSS and wider data protection trends.
In conclusion, being compliant with PCI-DSS not only ensures the protection of ‘Cardholder Data’ but also shields your business from the harsh outcomes of non-compliance. It’s not just about adhering to industry standards; it’s about providing customers with the security they deserve. As businesses increasingly operate in a digital environment, ensuring the safe handling of cardholder data should be a top priority. Likewise, compliance with PCI-DSS helps to build trust with customers and boosts the overall reputation of the business.











[…] the currency of today’s digital information age, data, specifically cardholder data, has become a critical asset that demands rigorous protective measures. The indispensable guide, […]
[…] the cost of implementing secure network systems, developing secure systems and applications, encrypting transmission of cardholder data, and regular updates and patch […]
[…] PCI-DSS stands for Payment Card Industry Data Security Standard. This is a globally recognized set of requirements intended to ensure that businesses that process, store, or transmit credit card information maintain the highest level of data security. […]
[…] you with knowledge, tools, and confidence necessary to secure your payment card transactions, protect cardholder data, and align your company with global data security standards, thus enhancing your business’ […]
[…] of security. The standards are broad, encompassing areas such as network security, data protection, vulnerability management, access control, network monitoring, and information security […]
[…] play a substantial role in the validation process by ensuring that their payment systems adhere to PCI-DSS requirements. By regularly reviewing and updating their systems, merchants can prevent potential vulnerabilities […]
[…] “Essential Security Technologies for PCI-DSS compliance“, a meticulous examination of pivotal security technologies necessary for adhering to Payment […]