“Unveiling the Common Pitfalls During a PCI-DSS Audit” seeks to shed light on the habitual slip-ups that can occur during a Payment Card Industry Data Security Standard (PCI-DSS) audit. As you navigate your way through the complexities of securing cardholder data, this in-depth guide lays out the potential errors and provides effective remedies to ensure a successful audit. Recognizing these pitfalls can be instrumental in fortifying your card data environment, safeguarding customer information, and upholding industry standards, thus enhancing your company’s credibility.
This image is property of www.frazierdeeter.com.
Lack of Understanding or Misinterpretation of PCI DSS Requirements
Maintaining compliance with the Payment Card Industry Data Security Standard (PCI DSS) is paramount for businesses that handle cardholder data. However, common pitfalls during a PCI-DSS audit often root from a lack of understanding or misinterpretation of the requirements.
Not understanding the language and understating of requirements
You might find the language and terminologies stipulated in PCI DSS requirements intricate or ambiguous, leading to understating or not fully comprehending the requirements. This is indeed a major pitfall during a PCI-DSS audit as it forms the basis of your compliance pursuit. Hence, it’s critical to clearly understand these requirements or seek expert help for clarification where needed.
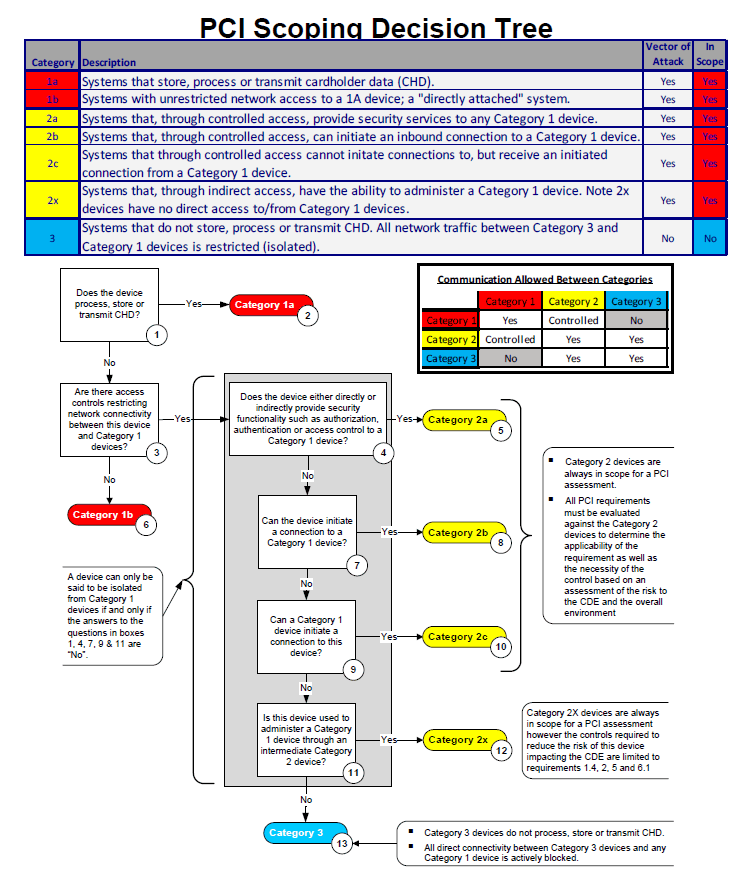
Misinterpretation of the ‘scope’ of PCI DSS
Another common misunderstanding is about the ‘scope’ of PCI DSS. It is possible that you might under or overestimate the scope, leading to unnecessary workload or noncompliance risks respectively. Proper scope definition is critical as it guides you on what systems and processes need to be protected, in line with PCI DSS regulations.
Failure to implement requirements due to misinterpretation
Misinterpretation of PCI DSS requirements might lead to failure in implementing them appropriately. This is another significant shortcoming in audit procedures and might expose your business to data breaches, fines and damaged reputation. Hence, ensure a correct comprehension and effective implementation of the requirements to avoid these hazards.
Neglecting to Maintain an Accurate and Up-to-date Network Diagram
Maintaining an accurate and up-to-date network diagram is a critical requirement of PCI DSS. Any neglect in this area can lead to big issues during an audit.
Inadequate documentation of Cardholder data flow
Without thorough documentation of cardholder data flow, there is a risk of data leaks. This inadequate documentation can make it difficult to identify where potential vulnerabilities may exist within your network, making it easier for malicious actors to exploit these weaknesses.
Failure in identifying all systems involved in the processing of Cardholder data
Each system involved in processing cardholder data should be included in the network diagram. Failure to identify all such systems can lead to them being left unprotected, creating potential points of vulnerability within your network.
Underestimation of importance of network diagram
While it might seem like a tedious task, the importance of maintaining a comprehensive network diagram cannot be underestimated. This diagram is crucial when it comes to identifying and managing risks associated with data security, and neglecting it can have severe consequences on your PCI DSS compliance posture.
Ineffective Risk Assessment Process
Risk assessment is an integral part of maintaining PCI DSS compliance. However, an ineffective risk assessment process can cause severe pitfalls during a PCI-DSS audit.
Overlooking vulnerabilities in systems and processes
Even small vulnerabilities in your systems and processes can lead to large breaches. It is essential to conduct a thorough risk assessment to identify all potential vulnerabilities and mitigate them effectively.
Failure to properly identify and assess risks
Misjudging a particular risk, or failure to identify certain risks altogether, can lead to cybersecurity incidents. Therefore, a comprehensive and systematic risk identification and assessment process is vital for effective data security.
Insufficient risk-control measures leading to potential breaches
Inadequate risk-control measures can be likened to a broken dam – susceptible to breaches. Proper risk-control measures ensure potential vulnerabilities are effectively managed and any threats are promptly detected and mitigated.
Failure to Execute Regular Testing and Monitoring
Testing and monitoring are valuable methods to ensure your cybersecurity measures are effective. Any failure in regular execution can expose your systems to unnecessary risks.
Insufficient or irregular vulnerability scanning and penetration testing
Irregular scanning or penetration testing could delay the detection of vulnerabilities in your systems. Conducting these confirmatory tests regularly ensures a lower probability of undetected threats.
Ignoring the importance of ongoing monitoring of security controls
Ongoing monitoring of security controls can uncover any anomalies in your network. Ignoring this requirement might result in overlooked threats and delayed response, making your systems more susceptible to breaches.
Delay in identifying and addressing vulnerabilities due to lack of regular testing
A lapse in regular testing and monitoring can delay identifying and addressing vulnerabilities. This can enhance the duration a threat goes undetected, thereby increasing potential damages.
This image is property of www.frazierdeeter.com.
Non-compliance with Access Control Measures
Access control measures are crucial for safeguarding sensitive cardholder data. Any non-compliance with these measures can lead to substantial risks of data breaches.
Lax controls over access to Cardholder data
Loose controls over access to cardholder data could allow unauthorized users to access and misuse this sensitive information. Strict access controls are crucial to prevent such instances.
Neglecting to implement strong access control measures
Neglecting to implement strong access control measures could allow easy access to sensitive data. This could lead to data breaches, causing reputational damage and non-compliance penalties. Hence, it is crucial to implement strong access controls as part of your cybersecurity strategy.
Failure to maintain and monitor access logs
Access logs are essential for tracking who accesses your data. Failure to maintain and monitor these logs might hinder efforts to investigate and resolve any breaches. It’s vital to regularly review these logs to promptly identify and counter any unauthorized access.
Lack of Proper Encryption Standards
Encryption is a vital data protection measure. However, any non-compliance with appropriate encryption standards could put your sensitive cardholder data at risk.
Non-compliance with encryption standards for data transmission
PCI DSS requires encryption for data at rest and during transmission. Failing to comply with these encryption standards could expose your data during transmission, leading to potential data breaches.
Failure to properly manage encryption keys
Managing encryption keys is equally critical as the encryption itself. Inadequate management could result in unauthorized access to encrypted data, thereby rendering the encryption useless.
Misunderstanding the importance of encryption in protecting Cardholder data
Encryption is a critical element of data security, and any misunderstanding or devaluation of its importance could lead to use of weak or inappropriate encryption measures. This could make your data easier to decrypt and exposed to potential breaches.
This image is property of www.dnsstuff.com.
Not Implementing Adequate Incident Response Plan
Having an efficient incident response plan is a crucial requirement of PCI DSS. Any gap in its implementation could hamper your ability to efficiently resolve data breaches.
Lack of incident response plan in case of data breaches
Without an appropriate incident response plan, your organization might struggle to contain and mitigate a data breach. Such a scenario could cause a prolonged resolution time, causing greater damage and reputational harm.
Failure to adequately train personnel on incident response processes
An incident response plan is only as good as the individuals implementing it. Failing to adequately train your personnel can cause a delay and inefficiency in resolving incidents, thereby leading to potential compromises of sensitive data.
Inefficient response to incidents leading to potential data compromises
Inefficient responses to data incidents could lead to significant data compromises. This could subsequently lead to reputational damage, financial losses, and non-compliance penalties. Therefore, implementing an efficient and effective incident response plan is crucial.
Inadequate PCI DSS Training for Employees
Employee awareness and training are vital in maintaining PCI DSS compliance. However, inadequate training can cause significant pitfalls during a PCI-DSS audit.
Failure to provide sufficient training and awareness to staffs
Lack of sufficient training could lead to employee mistakes and oversights, thereby exposing your systems to vulnerabilities. Therefore, regular and detailed training sessions for all staff handling cardholder data are highly necessary.
Ignorance of employees’ role in maintaining PCI DSS compliance
Not understanding their role in maintaining PCI DSS compliance might make your employees ignorant of their responsibilities. Such ignorance could lead to disregard for complying with the necessary regulations, causing potential breaches.
Lack of regular PCI DSS information sessions
Regular PCI DSS information sessions can keep all employees updated on the latest requirements, threats, and best practices. Lack of these sessions can cause a gap in awareness, which might result in potential non-compliance issues.
This image is property of marvel-b1-cdn.bc0a.com.
Not Maintaining Compliance Continuously
PCI DSS compliance is not a one-time project, but a continuous pursuit. However, neglecting continuous monitoring of compliance might lead to serious pitfalls during an audit.
Consideration of PCI DSS as a one-time project
Seeing PCI DSS compliance as a one-time project can result in outdated protection measures and systems, leading to potential vulnerabilities. Regular reviews of your compliance status and timely updates are necessary to prevent such lapses.
Overlooking the need for regular compliance reviews
Without regular compliance reviews, it becomes difficult to identify and address any lapses promptly, thereby potentially exposing sensitive data to breaches. Always ensure that your compliance is constantly reviewed and updated for optimal data security.
Ignoring changing requirements of PCI DSS standards
PCI DSS standards are continually updated to counteract emerging threats. Ignoring such changes may render your protective measures ineffective. Hence, always keep an eye on evolving PCI DSS regulations and promptly incorporate any changes into your data protection program.
Over-reliance on Third-party Service Providers
Reliance on third party service providers can help ease the burden of maintaining PCI DSS compliance. However, entirely relying on them can risk non-compliance.
Failure to understand the extent of responsibility despite outsourcing
Outsourcing PCI DSS functions does not eliminate your responsibility for ensuring compliance. Failing to fully comprehend this responsibility can lead to relying too heavily on third-party service providers, bypassing your own due diligence which is essential for maintaining compliance.
Neglecting the role of service providers in maintaining compliance
Without considering the role of your service providers in maintaining compliance, you run a risk of them not implementing necessary controls leading to potential data breach risks. Ensure your providers are effectively implementing PCI DSS requirements.
Assuming third-party providers are automatically PCI DSS compliant
Just because a service provider is reputable or large scale, do not assume they are automatically maintaining PCI DSS compliance. Validate their compliance level regularly to avoid any potential breaches due to their non-compliance.