Embarking on the task of conducting a risk assessment under the Payment Card Industry Data Security Standard (PCI-DSS) can seem like a daunting prospect. Nevertheless, this distinct process plays a crucial role in protecting sensitive cardholder data and ensuring compliance. “Understanding the Procedure: How are Risk Assessments Conducted under PCI-DSS?” unravels this intricate process, shedding light on the strategic methods and key steps involved in successful PCI-DSS risk assessment. It explores the multiplicity of factors that need to be evaluated, from establishing the assessment scope to analyzing and mitigating potential risks. Grasping the specifics of this process allows you to navigate with confidence, safeguarding your business and your customers’ valuable information.
Understanding PCI-DSS
Payment Card Industry Data Security Standard (PCI-DSS) is a set of security standards that businesses must comply with to ensure the safe handling of sensitive data. In this guide, you will learn about what PCI-DSS is, why it is important, and how to comply with its requirements.
Definition of PCI-DSS
PCI-DSS stands for Payment Card Industry Data Security Standard. This is a globally recognized set of requirements intended to ensure that businesses that process, store, or transmit credit card information maintain the highest level of data security.
The Purpose of PCI-DSS
The primary purpose of PCI-DSS is to reduce the risk of debit and credit card data loss. It provides an actionable framework for developing a robust payment card data security process. This includes prevention, detection, and appropriate reaction to security incidents.
Organizations That Need to Comply with PCI-DSS
If your organization processes, stores, or transmits credit or debit card data, you need to comply with PCI-DSS. This applies to all merchants, regardless of size or volume of transactions, who accept, transmit, or store any cardholder data from any card branded with the logo of one of the major card brands.
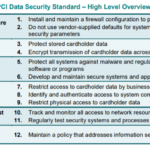
Key Provisions in PCI-DSS
The PCI-DSS has twelve key requirements under four broad objectives. Collectively, these requirements ensure the security of cardholder data.
Protection of Cardholder Data
PCI-DSS mandates encryption of cardholder data across open, public networks to uphold confidentiality. Businesses should ensure that any transmitted data is secure, and storage of sensitive data is kept to a minimum and always encrypted.
Maintain a Secure Network
The PCI-DSS requires organizations to, among other things, have a firewall in place and change vendor-supplied defaults before installing a system on the network to make it secure.
Implement Strong Access Control Measures
Access to system resources and cardholder data should be restricted. Every individual with computer access should have a unique ID and a secure password.
Maintain an Information Security Policy
A documented information security policy should be disseminated to all employees. This policy defines the company’s approach to information security and also dictates the acceptable use of technology resources.
Importance of Risk Assessment in PCI-DSS
Risk assessments are crucial components of PCI-DSS compliance. These assessments aim to identify, analyze and evaluate risks to cardholder data within the organization.
Identifying Vulnerabilities
Risk assessments help firms to identify security vulnerabilities in their cardholder data environment. These vulnerabilities could be weaknesses in security procedures, system design, or internal controls that could be exploited.
Establishing Impact Levels
Risk assessments also establish the potential impact on an organization if the identified vulnerabilities were to be exploited. Risks are typically assessed in terms of their potential effect on cardholder data.
Highlighting Risk Treatment Strategies
Highlights of the risk treatment strategies include measures that organizations need to take to minimize, avoid, transfer or accept identified risks.
The Step-by-Step Process of PCI-DSS Risk Assessment
Risk assessments are not once-off activities. They require a strategic approach, involving several steps.
Asset Identification
You need to identify all assets that involve cardholder data or could impact the security of cardholder data. This includes physical, information, software, and human resources.
Threat and Vulnerability Identification
Thoroughly explore and document the potential threats to each asset and the vulnerabilities that could be exploited.
Risk Determination
This involves quantifying the risk posed by each threat and vulnerability. Multiple factors are considered, including the likelihood of the threat occurring, the potential impact on the organization, and the ability of the controls to resist the threats.
Risk Mitigation and Treatment
Decide how to address each risk, considering your organization’s size, complexity, and risk tolerance. Also, look into ways to minimize the risk effects.
Risk Evaluation and Review
After your risk mitigation strategies are in place, review and re-evaluate your risk assessment. Repeat the risk assessment process to ensure that you have not overlooked any areas and to keep up with changes in the risk environment.
Asset Identification in PCI-DSS Risk Assessment
Asset identification is a critical first step in risk assessment. It involves taking stock of all the resources in an organization.
Identifying all Possible Assets
All the assets that could in any way involve cardholder data need to be identified. These may include but are not limited to systems, network devices, card readers, databases, hard drives, and paper records.
Classifying Assets
Once all the assets have been identified, they need to be classified based on criteria such as their function, owner, location, or information sensitivity level. This helps in prioritisation during the risk assessment process.
Assigning Asset Ownership
Each identified asset should have a designated owner. The asset owner is the individual or entity with the responsibility and authority to manage the security controls for that asset.
Threat and Vulnerability Identification in PCI-DSS Risk Assessment
Threat and vulnerability identification is an essential part of the risk assessment process.
Understanding the Concept of Threats and Vulnerabilities
A threat in the PCI-DSS context is a circumstance or event with the potential to cause harm to a system or network by tainting the confidentiality, availability, or integrity of cardholder data. A vulnerability is a weakness in a system or its design that could be exploited by a threat.
Identifying Potential Threats and Vulnerabilities
It involves documenting possible threats like hackers, malware, dishonest employees, and system faults. Vulnerabilities could be inadequate network security, weak passwords, unpatched systems, or lack of personnel awareness.
Assessing the Likelihood of Threat Occurrence
Evaluate how likely it is for the threat to exploit the vulnerability. Look at factors such as the extent and nature of vulnerabilities, the capabilities of the threat sources, and the existing controls.
Risk Determination in PCI-DSS Risk Assessment
After identifying threats and vulnerabilities and judging the likelihood of occurrence, proceed to calculate risk ratings.
Calculation of Risk Ratings
Risk rating is the product of the values of likelihood and potential impact. A commonly used rating scale is high, medium, and low.
Understanding High, Medium, and Low Risks
High risks are those with significant potential impact and a high likelihood of occurrence. Medium risks have moderate potential impact and likelihood. Low risks have minimal potential implications and a low likelihood of being exploited.
Risk Mitigation and Treatment in PCI-DSS Risk Assessment
Risk mitigation and treatment are the steps taken to deal with the identified risks.
Selecting Appropriate Risk Treatment Options
There are several ways to treat risks: mitigate the risk by implementing controls, avoid the risk by not engaging in the risk-prone act, transfer the risk to a third party, or accept it if it’s within the risk tolerance.
Implementation of Risk Mitigation Measures
Risk mitigation measures often involve implementing security controls to reduce the risk to an acceptable level. These controls can be administrative, technical, or physical.
Creating Risk Mitigation Plans and Schedules
Establish an action plan for each risk, outlining the steps to be taken, resources required, responsible parties, and timelines.
Risk Evaluation and Review in PCI-DSS Risk Assessment
The PCI-DSS requires ongoing monitoring and evaluation of the risk environment to ensure that controls continue to be effective.
Periodic Risk Assessment Reviews
Regularly review risk assessments to identify any changes in the risk environment, effectiveness of adopted risk treatment options, and compliance status with the PCI-DSS.
Re-evaluation and Updating of Risk Assessment
If significant changes occur in the business environment or cardholder data environment, perform a re-evaluation of the risk assessment.
The Role of Third-Party Service Providers in PCI-DSS Risk Assessment
Where necessary, organizations can employ third-party service providers to help with PCI-DSS risk assessments.
Choosing the Right Service Provider
When choosing a service provider, consider their experience, expertise in PCI-DSS, track record, and cost. It’s crucial to hire someone you trust because they will access sensitive data.
The Role of Service Providers in Risk Assessment
A service provider can provide valuable insights and advice during the risk assessment process given their broad perspective and experience. They can identify assets, threats, and vulnerabilities you might miss, help calculate risk levels, and suggest suitable risk treatment options.
Managing the Relationship with Your Service Provider
Maintain a cooperative and collaborative relationship with your service provider. Provide them with the necessary information to do their job, and make sure to implement the control measures they recommend. Review their performance periodically to ensure they meet your needs.