In the increasingly complex landscape of digital security, maintaining compliance with Payment Card Industry Data Security Standard (PCI-DSS) is of paramount importance for businesses. The essential aspect covered in this article is the crucial role that continuous monitoring plays in ensuring uninterrupted compliance with these standards. It is designed to provide you, as a professional seeking comprehensive insights, with a thorough understanding of how ongoing vigilance assists in maintaining a robust and secure card payment environment.

Overview of PCI-DSS Compliance
In the contemporary digital ecosystem, safeguarding sensitive data is paramount. One vital aspect of this is adhering to the Payment Card Industry Data Security Standard (PCI-DSS) regulations. Before delving into the intricacies of PCI-DSS and the role that continuous monitoring plays in its compliance, let’s build an understanding from the ground up.
Understanding the concept of PCI-DSS Standards
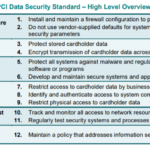
The PCI-DSS Standards are a comprehensive set of prescribed norms conceptualized by leading card service providers like Visa, Mastercard, and American Express. These regulations form the benchmark to protect cardholder data and prevent fraudulent activities related to card transactions.
Why businesses need to comply with PCI-DSS
compliance with PCI-DSS is not just about fulfilling an obligatory regulation but is a necessity for organizations. It creates a trusted business environment for customers, demonstrating that their sensitive card details are in safe hands in any digital transaction. Non-compliance can lead to exorbitant penalties, declined reputation, and loss of business.
Significance of PCI-DSS on securing cardholder data
The PCI-DSS integrates stringent safety controls to protect cardholder data. Complying with these standards ensures the reduction of vulnerabilities in the system, by strengthening security architecture. It mitigates the potential of data breaches, and promotes customer trust.
Necessity of Continuous Monitoring in PCI-DSS
When it comes to compliance with PCI-DSS, continuous monitoring is an indispensable part. It requires a dedication that is aligned with the organization’s commitment to data privacy and security.
Relevance of continuous monitoring in maintaining compliance
Continuous monitoring provides an ongoing and real-time analysis of security controls. It ensures that an organization’s systems adhere to PCI-DSS rules consistently, thereby maintaining their compliance status.
Correlation between persistent monitoring and data security
The continuous monitoring process involves regular assessment, reporting, and improving security measures, thereby heightening data security. It offers a thorough understanding of the data flow, identifying any potential loopholes that may lead to security breaches.
Differentiating continuous monitoring from periodic audits
While both continuous monitoring and periodic audits are necessary, they are not the same. Continuous monitoring is an ongoing process, whereas, an audit is a scheduled activity. The former offers real-time insights into security systems, whereas audits analyze the security status at a specific point in time. Together, they establish a robust security ecosystem.
Components of Effective Continuous Monitoring
An effective continuous monitoring system comprises several critical components.
Critical elements in a continuous monitoring framework
The critical elements of the monitoring framework must include risk assessment, a secure configuration management, vulnerability scanning, and real-time alerts. It’s imperative to have a well-crafted incident response plan for prompt and efficient mitigation of risks.
Relation of these components to PCI-DSS compliance
Each component lends strategic value to the maintenance of PCI-DSS compliance. For instance, vulnerability scanning helps comply with PCI-DSS regulations about regular network testing, while incident response planning aligns with its requirement for efficient detection and mitigation of security threats.
How components support in managing risk and enhancing security posture
Components of the continuous monitoring system work collaboratively to manage and mitigate risk. They offer constant visibility into the system’s security status, enabling organizations to timely identify and rectify vulnerabilities, thereby enhancing their security posture over time.
Implementing Continuous Monitoring for Compliance
The approach to continuous monitoring implementation should be systematic and well-planned.
Steps to implement a continuous monitoring program
Successful implementation calls for mapping out the organizational infrastructure, identifying sensitive data resources, setting up the required security controls and tools, and training the team for proficient handling of the security infrastructure.
Stages involved in maintaining PCI-DSS compliance
After initial implementation, maintaining compliance involves running regular assessments, reassessing risks, maintaining and updating security measures as needed, and continually monitoring the environment for potential threats.
Strategies to maximize the effectiveness of continuous monitoring
Maximizing effectiveness of continuous monitoring involves regular updating of monitoring tools, running periodic system reviews, defining clear incident response protocols, and providing continued training to the team handling security controls.
Impact of Technology and Automation in Continuous Monitoring
In the era of rapidly advancing technology, it has a profound impact on continuous monitoring, particularly automation.
Role of automation tools in enhancing continuous monitoring
Automation tools simplify the process of continuous monitoring by reducing manual labor, improving accuracy and speed of the monitoring process. Additionally, they assist in consolidating and analyzing data, making it easier to track the compliance status.
How technology simplifies compliance process
In addition to reducing effort and increasing speed, technology aids in the dual factor authentication, encryption-decryption processes, and real-time generation of compliance reports, thereby simplifying the overall compliance process.
Use of advanced technological solutions such as AI in compliance monitoring
The deployment of Artificial Intelligence (AI) in compliance monitoring provides unprecedented accuracy and predictive capabilities. Machine learning algorithms aid in identifying patterns and predicting potential security threats, leading to proactive management of security risks.
Metrics for Evaluating Continuous Monitoring Success
Evaluation of the continuous monitoring system offers insights into its efficiency.
Determining effective measures for continuous monitoring
Effective measures can range from the number of identified vulnerabilities, incidents detected and resolved within a specific timeframe, to system downtime. The chosen metrics should be relevant, measurable, and should provide a comprehensive snapshot of the system’s security status.
Impact of monitoring metrics on maintaining compliance
These metrics play a critical role in measuring the effectiveness of the monitoring system and assessing alignment with PCI-DSS requirements. They assist in identifying areas of non-compliance, thereby prompting rectifications and enhancements.
Methods to maximize monitoring performance using metrics
Regular review and analysis of these metrics should be undertaken to enhance performance. Doing so will aid in pinpointing inconsistent areas that need attention for improved efficiency and system optimization.
Mitigating Risks with Continuous Monitoring
Continuous monitoring plays a key function in risk management and mitigation.
Understanding risk in PCI-DSS context
In the context of PCI-DSS, risk refers to any potential threat that can exploit vulnerabilities in the payment card industry’s digital infrastructure leading to a data breach.
Utilizing continuous monitoring to mitigate potential risks
Continuous monitoring allows businesses to stay a step ahead, by offering real-time visibility into system vulnerabilities, potential threats, and anomalous activities. This proactive stance aids in mitigating risks effectively.
How continuous monitoring helps in early detection and resolution of risks
With alerts and alarms configured in the continuous monitoring system, organizations can quickly detect and mitigate threats. Thereby, lesser downtime and minimized loss.
Case Studies: Benefits of Continuous Monitoring in PCI-DSS Compliance
Real-life case studies underscore the importance of continuous monitoring in enhancing security compliance.
Studying successful instances of organizations implementing continuous monitoring
Successful implementations have demonstrated how continuous monitoring has dramatically reduced instances of data breaches and fraudulent activities, fortifying the organization’s security architecture.
Lessons learned from these case studies
Every successful implementation or data breach makes a strong case for the importance of a well-implemented continuous monitoring system and regular staff training. It highlights best practices, or potential pitfalls, providing valuable guidance for other organizations.
Implementing these learnings in your own organization
It’s important to incorporate these learnings to build better and more robust systems in your organization. It can prevent potential losses and accelerate the growth of the organization’s security posture.
Challenges and Solutions in Continuous Monitoring for Compliance
Implementation of continuous monitoring can present its own set of challenges.
Identifying potential challenges in the implementation process
A few potential challenges include the acquisition and training of capable personnel, budget constraints, ensuring accuracy of automated systems, and staying updated with ever-evolving security threats and changes in compliance norms.
Proposing solutions to tackle these obstacles
Overcoming these challenges involves investment in employee training, making a cost-benefit analysis to ensure budget allocation towards upgraded security infrastructure, maintaining redundant systems for accuracy checks, and staying informed about industry development.
Learning from industry best practices
Industry best practices act as guiding lights towards the successful implementation of continuous monitoring systems. They bring into focus tried and tested solutions and provide valuable insights derived from industry veterans, which can be tailored to an organization’s specific needs.
Future of Continuous Monitoring in PCI-DSS Compliance
The landscape of data security is dynamic.
Evolving trends in the compliance and security landscape
Trends towards machine learning-enhanced security measures, usage of predictive algorithms, and integration of compliance to drive business performance, are changing the security and compliance landscape.
Predicting the future role of continuous monitoring
Continuous monitoring will continue to be a bulwark in maintaining security and compliance, but with amplified efficiency and intelligence, courtesy of AI and machine learning advancements.
How organizations need to adapt for future security challenges in PCI compliance
Keeping pace with the cybersecurity landscape is pivotal. Organizations need to stay aware of evolving threats. They should invest in advanced technical solutions, train their team to handle these new tools, and focus on integrating security and compliance measures with the overall business strategy going forward.
In conclusion, continuous monitoring is a lynchpin in ensuring PCI-DSS compliance. It needs to be ingrained in organization systems, processes, and culture. With diligent implementation, continuous monitoring contributes significantly to the enhancement of the organization’s security architecture.