As a software professional, the contemporary financial landscape necessitates your comprehension of the specifications inherent in software development under the Payment Card Industry Data Security Standard (PCI-DSS). This valuable perspective, aptly titled “Understanding the Requirements for Software Development under PCI-DSS”, offers a concise exploration into the intricate standards, guidelines, and controls required in PCI-DSS compliant software development. From data encryption standards to comprehensive vulnerability management programs, this article presents the essentials you need to know to comply with PCI-DSS.

Understanding PCI-DSS
PCI-DSS stands for Payment Card Industry Data Security Standard. This is a comprehensive set of requirements for enhancing payment account data security. It was developed by the founding payment brands of the PCI Security Standards Council, namely American Express, Discover Financial Services, JCB International, MasterCard Worldwide, and Visa Inc International to foster wide-scale adoption of consistent data security measures globally.
Definition and purpose of PCI-DSS
The primary purpose of the PCI-DSS is to reduce the risk of debit and credit card data loss. It applies to all entities that store, process, or transmit cardholder data and has been endorsed by all the major card brands. These organizations are obligated to comply with various security measures, thereby ensuring that their customers’ transactions are secure and their personal data protected.
Importance of PCI-DSS in software development
In software development, PCI-DSS is of essence because any software dealing with credit or debit card information must observe these regulations to protect cardholder data. Non-compliance can lead to serious repercussions including financial penalties, increased transaction fees, and potential loss of ability to process payments which could damage the reputation of the business.
Entities that require PCI-DSS compliance
Entities that require PCI-DSS compliance are diverse and include merchants, financial institutions, point-of-sale vendors, and hardware and software developers. Any entity that stores, processes, or transmits payment cardholder data is required to be PCI-DSS compliant.
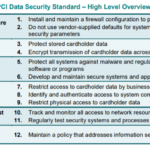
Essential Requirements of PCI-DSS in Software Development
Security Management
Effective security management involves the orchestration and organization of a security program. This includes implementing a firewall configuration, maintaining a vulnerability management program, and using strong cryptography to protect sensitive data during transmission.
Policy Maintenance
Policy maintenance under PCI-DSS involves regularly updating and analyzing the security policies to ensure they are adequate and effective. It also includes establishment of information security policies and assigning responsibilities for all tasks.
Risk Assessment and Management
Risk assessment involves identifying and assessing the risks that pose a significant threat to the cardholder data. It includes creating a risk mitigation and management plan to address each identified risk.
Vulnerability Management
Vulnerability management entails implementing controls to detect and mitigate potential system vulnerabilities. This includes regular system testing, doing security systems and processes assessments as well as monitoring and addressing detected vulnerabilities.
Requirements for Software Applications under PCI-DSS
Data Protection Requirements
Data protection under PCI-DSS involves putting stringent measures in place to safeguard sensitive data. It involves cardholder data encryption, hashing or using dummy data for testing, and restricting data retention to minimum required elements for business as per the data retention policy.
Encryption and Key Management
Proper encryption and key management help protect data in transit across public networks. It involves using strong cryptographic keys, secure cryptographic key management systems and adhering to industry best practices on cryptography.
Access Control Requirements
Access control under PCI-DSS is about restricting access to cardholder data to only authorized personnel. It involves assigning a unique ID to each person with computer access and restricting physical access to cardholder data.
Tracking and Monitoring Access
In the context of PCI-DSS, tracking and monitoring of access is essential to ensure only authorized individuals have access to systems that store, process, or transmit cardholder data. It entails regularly monitoring and tracking all access to network resources and cardholder data.
Awareness and Training of Staff
Awareness and training under PCI-DSS involve training employees on security protocols. Equipping staff members with awareness, education, and training also helps them better understand the operational impact of PCI-DSS and thus, be better equipped to ensure and maintain compliance.
Handling Sensitive Data under PCI-DSS
Data Classification and Handling
Data classification and handling refers to recognizing and separating sensitive data from non-sensitive data. It involves determining the value and sensitivity level of data, which then guides the necessary protection mechanisms.
Data Encryption and Key Management
Data must be encrypted using strong algorithms while in transit, at rest or on portable digital media. PCI-DSS guidelines provide specific measures for key management, including generation of strong cryptographic keys, secure distribution of keys, and storage of keys in the fewest locations possible.
Managing storage and disposal of sensitive data
PCI-DSS guidelines require data retention and disposal policies to minimize storage of cardholder data. When data is no longer required, it must be disposed of securely so it cannot be reconstructed.
Secure Software Development Lifecycle (SDLC) under PCI-DSS
Secure Design
Secure design encourages adherence to a set of principles during the design phase of the SDLC. It includes the incorporation of data protection requirements into the system architecture.
Secure coding practices
Secure coding practices under PCI-DSS ensure that software applications developed are free from security vulnerabilities. This includes following industry best practices such as OWASP guidelines, and adhering to coding guidelines to mitigate common coding vulnerabilities.
Testing and Validation
Software should be thoroughly tested to validate compliance with PCI-DSS requirements. This includes conducting vulnerability scans and penetration tests to identify potential security weaknesses.
Post-Implementation Review
A post-implementation review under PCI-DSS involves a thorough review and analysis of the software operations to ensure it meets all PCI-DSS requirements. This process helps in identifying potential gaps or weaknesses in the SDLC process and correcting them for future iterations.
Role of QA in Ensuring PCI-DSS Compliance
Quality Assurance Strategy
Quality assurance (QA) strategy plays a critical role in ensuring PCI-DSS compliance, as the QA team needs to validate the software’s functionality while ensuring compliance with standards. This includes developing test plans and evaluating the software to ensure it meets all requirements of PCI-DSS.
Testing against PCI-DSS Requirements
The QA team must perform a variety of tests against PCI-DSS requirements to validate software compliance. These tests include functional testing, security testing, penetration testing, and vulnerability assessment.
Continuous Monitoring and Auditing
Continuous monitoring and auditing under the purview of QA helps identify and rectify non-compliance issues timely. It involves regular monitoring and review of controls to ensure continued effectiveness and appropriateness.
Role of IT Infrastructure in PCI-DSS Compliance
Network Security Requirements
Network security is vital in PCI-DSS compliance. It involves securing systems and networks against unauthorized access, misuse, or destruction. This includes installation and maintenance of firewall configurations to protect cardholder data, implementation of antivirus software, and secure system configurations.
Physical and Hardware Security
Physical and hardware security requirements under PCI-DSS entail protecting the physical devices and systems that store, process, or transmit cardholder data. This includes securing the hardware, maintaining secure systems, and ensuring proper user access controls.
Server Configuration and Security
Securing server configurations is crucial in meeting PCI-DSS compliance. It involves developing and maintaining secure systems and applications, conducting regular system updates to patch vulnerabilities, and restricting access to system components.
Role of Incident Management under PCI-DSS
Incident Response Planning
Effective incident response planning involves having a structured approach for addressing and managing the aftermath of a security breach or attack. It should include plans to address various types of incidents, regular testing and updating of the plan, and training and awareness.
Handling an Incident
Handling an incident under PCI-DSS involves a coordinated approach to manage the incident, minimise damage and downtime, and ensure return to normal operations as quickly as possible. It includes proper identification, containment, investigation, reporting, and recovery.
Post-Incident Recovery and Analysis
Post-incident recovery and analysis under PCI-DSS compliance ensures that the organization has learnt from the breach and put measures in place to prevent a recurrence. It includes a comprehensive review of the incident and measures taken, and updating security measures and processes to avoid similar incidents in the future.
Auditing and Reporting for PCI-DSS Compliance
Internal Auditing
Internal auditing is essential for PCI-DSS compliance as it provides the organization with an independent assessment of its adherence to PCI-DSS requirements and also helps in identifying areas of non-compliance and potential improvement.
Third-Party Auditing
Third-party auditing provides an external validation of an organization’s compliance with PCI-DSS. It involves the use of an independent body to conduct a thorough review and verification of the organizations’ security controls and procedures.
Reporting Compliance to Stakeholders
Keeping stakeholders informed of the PCI-DSS compliance situation through regular reports can build trust, demonstrate transparency and accountability, and ensure continued support.
Challenges in Ensuring PCI-DSS Compliance
Maintaining up-to-date compliance
This involves continuously staying abreast of PCI-DSS compliance requirements given the regularly updated standards. This calls for significant resources to keep up with the changes, implement them and ensure compliance is maintained.
Scaling Security with Business Growth
As businesses grow, scale, and expand their services, security needs to scale proportionately. Achieving this can be a challenge requiring strategic planning and resources to ensure PCI-DSS compliance is maintained.
Handling New Technologies and Methods
Rapid advancements in technology often present challenges in maintaining PCI-DSS compliance. Organizations must assess and manage the risks associated with new technologies and payment methods while maintaining the necessary levels of PCI-DSS compliance.