“Unlocking the Steps to Becoming PCI-DSS Compliant” demystifies the complex principles of Payment Card Industry Data Security Standard (PCI-DSS) compliance. This article provides a precise, step-by-step guide to help your business navigate through the multi-layered process of adopting PCI-DSS requirements. From the initial assessment to maintaining ongoing compliance, it empowers you with knowledge, tools, and confidence necessary to secure your payment card transactions, protect cardholder data, and align your company with global data security standards, thus enhancing your business’ trustworthiness in the market.
Understanding PCI-DSS
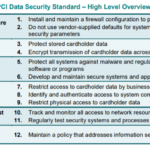
Comprehending the basics of PCI-DSS is prerequisite to becoming compliant. PCI-DSS stands for Payment Card Industry Data Security Standard, a global standard established to protect businesses and customers from data theft and fraud.
Defining PCI-DSS
PCI-DSS is a series of stringent security standards designed to ensure that all organizations that store, process, or transmit credit card information secure such data to protect consumers and reduce the risk of data breaches.
Importance of PCI-DSS Compliance
Complying with PCI-DSS is not only crucial for protecting customers and ensuring their trust but also mandatory for companies handling cardholder data. Non-compliance can lead to hefty fines, a potential loss of sales, lawsuits, a damaged reputation, and ultimately, business failure.
Businesses Affected by PCI-DSS
Every business, regardless of its size, that accepts card payments either online or offline, should comply with the PCI-DSS standards. This pertains to retailers, non-profit organizations, online stores, hotels, and virtually any business where cardholder data is stored, processed or transmitted.
Getting Started with PCI-DSS
Venturing into the world of PCI-DSS compliance might seem challenging. However, it starts with some simple steps that revolve around analyzing, evaluating, and preparing.
Analyzing Business Operations
Understanding your business operations is the first step. You should ascertain what type of cardholder data your business handles, which systems are involved, and how data flows through your organization.
Evaluating Current Security Measures
Next, assess your current security measures to identify which are appropriate for protecting cardholder data and where potential shortcomings may be. This includes both technological and procedural safeguards.
Developing a PCI-DSS Compliance Team
Identify key individuals from relevant departments within your organization to constitute a PCI-DSS compliance team. Assign responsibilities and set timelines for tasks to stay organized and focused.
Conducting a Gap Analysis
Gap analysis constitutes a vital part of the compliance process, allowing your organization to pinpoint vulnerabilities and determine how far you are from achieving compliance.
Purpose of a Gap Analysis
Conducting a gap analysis helps an organization identify vulnerabilities and weaknesses in its current system. It serves as the roadmap to close gaps between the current state and the desired compliant state.
Identifying Vulnerabilities and Weaknesses
Key areas to probe are unsecured databases, inadequate firewall protections, outdated systems, poor access controls, and under-par incident response plans.
Analyzing Risk Levels
Once vulnerabilities and weaknesses are recognized, evaluate the risk levels they pose to your business. This includes understanding how these issues may lead to potential breaches or losses and prioritizing them for immediate action.
Creating a PCI-DSS Compliance Plan
Once the groundwork has been laid, your organization needs to visualize a PCI-DSS compliance plan tailored to suit your business needs.
Outlining the Scope of Compliance
PCI compliance isn’t synonymous for all businesses, as the scope of compliance varies significantly depending upon the organization’s size, structure, and the nature of its operations.
Developing Compliance Goals
Create clear, actionable objectives to guide your journey to compliance. These goals need to meet PCI-DSS requirements and align with your organization’s overall security strategy.
Identifying Necessary Changes for Compliance
Recognize and document the changes necessary to meet your compliance goals. This could involve hardware and software upgrades, policy amendments, practice improvements, and staffing changes.
Implementing Security Policies and Procedures
Implementing robust security policies and procedures forms the backbone of your compliance initiative and helps protect your business from data breaches.
Creating a Network Security Policy
A network security policy is a critical document that outlines how you must handle, use, and manage your network infrastructure. It often includes protocols on password security, user responsibilities, and rules for system and device usage.
Establishing Access Control Measures
Access control is about ensuring that only authorized personnel have access to data and systems according to their role and necessity. This includes multifactor identification, restricted access to cardholder data, and strong password policies.
Developing Incident Response and Recovery Protocols
When breaches happen, a well-devised incident response plan can minimize damage. Include protocols for identifying, managing, and recovering from incidents in a timely and structured manner.
Securing Cardholder Data
Knowing how to securely manage cardholder data is a crucial aspect of PCI-DSS compliance.
Understanding Cardholder Data Protection
Cardholder data protection involves securing sensitive data using encryption, tokenization, and masking, limiting data storage and ensuring appropriate measures for data disposal.
Management of Cardholder Data
Manage cardholder data based on a need-to-know principle. Limit data storage to the minimum necessary, and secure disposal of data once it’s no longer needed.
Securing Physical Access to Cardholder Data
PCI-DSS compliance also mandates securing physical access to areas storing cardholder data, ensuring protection through surveillance systems, and implementing robust access-control mechanisms.
Upgrading Technology to meet PCI Standards
Meeting PCI-DSS standards often requires updates and upgrades to your organization’s technology stack, including security applications.
Identifying Necessary Technological Changes
Review your systems and note down outdated software, insufficient firewalls, or insecure data storage solutions that demand changes.
Updating and Patching Systems
Maintain up-to-date systems by regularly updating software and applying patches. This helps keep your systems secure from known vulnerabilities.
Encryption and Other Security Protocols
Implement security standards such as SSL/TLS, IPSEC, SSH to protect cardholder data. Encrypt data transmission across public networks and use secure methods for data storage.
Conducting Regular Audits and Testing
Regular audits and testing are critical for maintaining compliance and ensuring your security measures are functional.
Importance of Regular Audits
Audits provide a comprehensive view of your organization’s security posture, helping you stay alert to potential security risks.
Types of Auditing Testing
Conduct periodic penetration testing, vulnerability assessment and regularly review firewall and router configurations. Test security systems and processes at least quarterly or after any significant network changes.
Internal and External Auditing
Internal audits help maintain regulatory compliance throughout the year while third-party external audits provide an unbiased view of your compliance status.
Managing and Maintaining PCI Compliance
Maintaining PCI compliance demands continuous monitoring, swift responses to changes, and continual education.
Continuous Monitoring Strategies
Continuous monitoring includes keeping an eye on your networks, detecting unusual activity promptly, and taking quick actions in response.
Responding to Compliance Changes
As PCI-DSS standards update, your organization must adapt swiftly. Keep abreast with changes, and implement amendments promptly to stay compliant.
Educating Employees on Compliance
Regular training and awareness programs help employees understand their role in maintaining compliance and staying vigilant to potential security threats.
Working with a Qualified Security Assessor
A Qualified Security Assessor (QSA) can provide expert guidance, assisting your journey to compliance.
Choosing a Qualified Security Assessor
Select a QSA that fits your business needs in terms of experience, expertise, and understanding of your industry.
Role of a Qualified Security Assessor
A QSA will guide you throughout the compliance process, from conducting a gap analysis to preparing your compliance report.
Understanding Compliance Report
The compliance report, prepared by the QSA, comments on your compliance status and provides an action plan for achieving and maintaining compliance. Review it thoroughly, implement suggested changes, and keep it handy for reference.
PCI-DSS compliance is a fundamental obligation for businesses handling cardholder data. While the process may seem complex, breaking it down into manageable steps can simplify the journey. Prioritizing security and compliance not only safeguards your customers’ data but also preserves your business’s reputation and trust.