In the modern digital era, vigilance and innovation maintain the balance of data security. “Exploring the Impact of Virtualization and Cloud Services on PCI-DSS Scope” offers an incisive analysis on the evolution of Payment Card Industry Data Security Standard (PCI-DSS) in relation to the cutting-edge technologies of virtualization and cloud services. Your understanding of data security is poised for advancement as this concise discourse illuminates the progressive dynamic between these technological phenomena, and the subsequent implication on PCI-DSS scope, thus enhancing your resourcefulness to safeguarding sensitive cardholder data.

Understanding PCI-DSS
Definition of PCI-DSS
PCI-DSS refers to the Payment Card Industry Data Security Standard. This is a set of regulations formulated to secure credit and debit card transactions against data theft and fraud. It is a standard applied universally to all organizations that handle transactions from the major credit card brands.
Objective of PCI-DSS
The primary objective of PCI-DSS is to protect cardholder data. This is accomplished by maintaining a secure network, protecting cardholder data, managing a vulnerability program, employing strong access control and monitoring, and regularly testing systems. By adhering to these standards, organizations can maintain trust with their customers and prevent costly data breaches.
Key Requirements of PCI-DSS
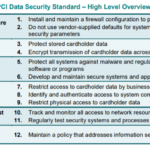
The PCI-DSS standard stipulates twelve key requirements grouped into six control objectives. These include creating and maintaining a secure network, protecting stored cardholder data, maintaining a vulnerability management program, implementing robust access control measures, regularly testing and monitoring networks, and maintaining a policy for information security.
Overview of Virtualization
Concept of Virtualization
Virtualization is a technology that involves creating virtual versions of computer hardware platforms, storage devices, and computer network resources. It enables running multiple operating systems and applications on the same server to enhance scalability and efficiency.
How Virtualization Works
Virtualization works by separating the physical hardware from a single computer, using a layer of software known as a hypervisor. The hypervisor allows the physical server to operate multiple virtual machines as standalone entities, each with its private set of virtual hardware resources.
Benefits and Risks of Virtualization
Virtualization offers several benefits, including cost-effectiveness, improved resource utilization, scalability, and quick deployment of new applications. However, it also carries risks, such as the complexity of managing virtual environments, potential performance issues, and the need for specialized expertise in understanding and controlling virtualization technologies.
Explaining Cloud Services
Defining Cloud Services
Cloud services refer to the delivery of services over the internet. They range from software solutions and data storage to servers and network functionalities. Cloud services allow businesses to access and store data on remote servers, reducing the need for maintaining physical, local servers.
Types of Cloud Services
There are three main types of cloud services: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). IaaS provides users with access to resources such as servers and storage, while PaaS offers a platform that allows users to develop, manage and run applications without the need to maintain the underlying infrastructure. SaaS is a software distribution model that delivers software applications over the internet.
Advantages and Disadvantages of Cloud Services
Advantages of cloud services include scalability, cost-effectiveness, accessibility from any location, and the constant availability of the most recent versions of software and platforms. However, disadvantages include potential security risks, dependency on internet connectivity, and potential loss of control over certain aspects of data management.
PCI-DSS Scope in Traditional IT Environment
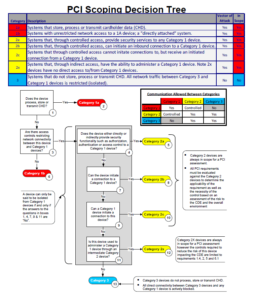
Identifying Cardholder Data Environment (CDE)
The Cardholder Data Environment is defined as the computer system components that store, process, or transmit cardholder data or sensitive authentication data, including any component that directly affects the security of this data.
Understanding System Components within the Scope
System components within the scope of PCI-DSS include network devices, servers, computing devices, and applications. All these components must be audited and verified for compliance with the PCI-DSS standards.
Defining PCI-DSS Compliance in a traditional Environment
PCI-DSS compliance in a traditional IT environment involves meeting all the 12 key requirements of the PCI-DSS standards. This includes developing and maintaining secure systems, protecting stored data, restricting access to cardholder data, regularly testing and monitoring network security, and maintaining a policy that addresses information security.
Implications of Virtualization on PCI-DSS Scope
Influence of Virtualization on Cardholder Data Environment (CDE)
Virtualization can amplify the complexity of the CDE because of the additional layers it adds to the infrastructure. The sharing of physical resources among multiple virtual machines makes the boundary of the CDE less distinct and more difficult to secure.
How Virtualization impacts System Components within the Scope
In a virtualized environment, system components within the scope of PCI-DSS include the virtual machines, hypervisors, host systems, applications, and network resources. All these components have to be individually controlled and monitored to ensure compliance with PCI-DSS requirements.
Ensuring PCI-DSS Compliance in a Virtualized Environment
Ensuring PCI-DSS compliance in a virtualized environment involves applying the same stringent security measures as in a traditional IT environment, but with special considerations for virtualization-specific risks. This includes isolating the cardholder data environment, implementing strong access control measures, and regularly testing and monitoring the virtualized system components.
Impact of Cloud Services on PCI-DSS Scope
Effects of Cloud Services on Cardholder Data Environment (CDE)
Cloud services can expand the CDE because the cloud is essentially an extension of the organization’s infrastructure. The use of third-party cloud providers can introduce additional risks and complexities, as the organization has to ensure that the provider meets all the necessary PCI-DSS requirements.
How Cloud Services Modify System Components within the Scope
In a cloud environment, system components within the scope can include the user interface, applications, database and storage, networking, and the many layers of the cloud provider’s infrastructure. As with the virtualized environment, all these components have to be separately controlled and monitored for PCI-DSS compliance.
Maintaining PCI-DSS Compliance in a Cloud Environment
Maintaining compliance in a cloud environment involves a shared responsibility between the cloud service provider and the user. However, it’s important to remember that the ultimate responsibility for compliance rests with the organization that holds the cardholder data itself.
Comparing the Impacts of Virtualization and Cloud Services on PCI-DSS Scope
Concurrent Effects of Virtualization and Cloud Services on CDE
Both virtualization and cloud services can complicate the CDE, but in different ways. Virtualization complicates the physical boundary definition, while cloud services complicate the control over the physical and logical boundaries due to the involvement of third-party service providers.
Differential Impacts on System Components within the Scope
In the case of virtualization, the primary impact is on the system’s physical components, while with cloud services, the impact is more on the logical separation of responsibilities and control between the user and the service provider.
Comparative Challenges in Ensuring PCI-DSS Compliance
When comparing virtualization and cloud services, the challenges posed by each can be different. With virtualization, the main challenge may be in ensuring that the hypervisor layer is secure. With cloud services, the main challenge usually lies in ensuring that the service provider is also fully compliant with PCI-DSS requirements.
Best Security Practices in Virtualization and Cloud Services
Security Features to Look for in Virtualization Solutions
In evaluating virtualization solutions, organizations should look for security features such as secure boot systems, reliable authentication and authorization mechanisms, data isolation, and encryption.
Recommended Security Measures for Cloud Services
On the other hand, when utilizing cloud services, organizations should maintain continuous oversight of the cloud provider’s compliance, use secure encryption methods for data transmission and storage, and ensure robust user access control measures are in place.
Encrypting Sensitive Data in both Environments
Regardless of the environment, whether virtual or cloud, data encryption is a crucial security measure. This involves converting data into a code to prevent unauthorized access, thereby providing an extra layer of protection for sensitive data.
Evolving Compliance Landscape with Virtualization and Cloud Services
Adjustments to PCI-DSS with Evolving Technologies
As technology evolves, the PCI-DSS standards also need to adapt. This will involve revising and updating the standards to ensure they cater to the nuances of emerging technologies including virtualization and cloud services.
Future Trends Impacting PCI-DSS Scope with Advancements in Virtualization and Cloud Services
The increasing use of virtualization and cloud services will undoubtedly impact the scope and application of PCI-DSS. Success with these technologies in the future will require a better understanding of their intricacies, and the development of more sophisticated and comprehensive security controls.
Preparing for Future Compliance Requirements
Organizations must stay abreast of these changes and tailor their security strategies to address the evolving challenges. They should also factor in these technological advancements when planning their security budgets to ensure that they can adapt to the changes and continue to meet compliance requirements.
Conclusion
Summarizing the Impacts of Virtualization and Cloud Services on PCI-DSS Scope
In conclusion, the adoption of virtualization and cloud services undeniably influences the overall scope of PCI-DSS. While they present various benefits in terms of operational efficiency and cost savings, they also introduce new complexities in defining and safeguarding the CDE and ensuring compliance.
Areas for Further Research
There is a pressing need for further research to understand and mitigate the unique security risks associated with these technologies and to develop flexible and robust security strategies that can accommodate their rapid evolution.
Closing Thoughts on PCI-DSS in a Virtual and Cloud-based Environment
As we move further into a digital age, it is essential that traditional cryptographic controls evolve alongside the trends in virtualization and cloud services. It will be critical for every organization dealing with cardholder data to balance these technologies’ benefits with the security requirements set out in the PCI-DSS standard.