Navigating the labyrinth of data protection can be a perplexing task, and understanding the pivotal function of the Payment Card Industry Data Security Standard (PCI-DSS) in the encryption of cardholder data is an integral part of this journey. The article entitled “Understanding the Role of PCI-DSS in Encryption of Cardholder Data” thoroughly examines how the PCI-DSS addresses the encryption of cardholder data, offering you comprehensive knowledge about the significance and application of this standard in securing cardholder information.
Understanding PCI-DSS
The concept of PCI-DSS
The Payment Card Industry Data Security Standard (PCI-DSS) is a set of guidelines designed to ensure all businesses that handle credit card information maintain a secure environment. PCI-DSS has been established by major credit card brands to protect against potential incidents of cardholder data theft. These standards aim to provide a comprehensive approach to securing card data across various channels, including storage, processing, and transmission.
Importance of PCI-DSS in the card payments environment
In our increasingly digital world, card payments have become the norm for various commerce activities. With this rising dependency on card transactions comes the threat of data breaches and identity theft. PCI-DSS plays a critical role in the card payments environment by ensuring businesses follow strict security measures when dealing with sensitive cardholder information. By complying with PCI-DSS standards, businesses can significantly reduce the risk of data breaches and avoid hefty penalties, while also fostering trust among their customers.
Components of the PCI-DSS standards
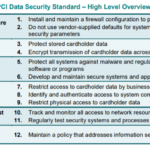
The PCI-DSS framework comprises 12 core requirements grouped into six control objectives. These include building and maintaining a secure network, protecting cardholder data, maintaining a vulnerability management program, implementing strong access control measures, regularly monitoring and testing networks, and maintaining an information security policy. Each of these requirements has specific sub-requirements that provide in-depth guidance on establishing a robust security posture.
PCI-DSS and Cardholder Data
Explanation of ‘Cardholder data’
Cardholder data refers to any information printed, processed, transmitted, or stored in any form on a payment card. This information typically includes the cardholder’s name, account number, expiration date, and the security code. In the context of PCI-DSS, cardholder data also encompasses sensitive authentication data, which includes full track data, PINs, and card verification codes.
Importance of securing cardholder data
Securing cardholder data is paramount to preventing data breaches and identity theft. As cyber threats continue to evolve, businesses must take proactive measures to protect sensitive customer data. Breaches can result in devastating financial loss, damage to a company’s reputation, and loss of customer trust. Therefore, securing cardholder data is not only about complying with laws and regulations but also about preserving consumer confidence and business integrity.
The relationship between PCI-DSS and cardholder data
PCI-DSS standards have been developed specifically to ensure the secure handling of cardholder data across its entire lifecycle. From the moment a card transaction is initiated to its processing, storage, and transmission, PCI-DSS ensures robust security measures are in place to protect this data. Adherence to these standards helps limit data breach opportunities and fortify consumer trust by demonstrating a commitment to safeguarding customer data.
Role of PCI-DSS in Encryption
Importance of encryption in data security
Encryption plays a crucial role in data security. It transforms intelligible data into a coded form, rendering it unreadable to anyone lacking the appropriate decryption key. This facilitates secure data transmission over unsecured networks and protects stored data from unauthorized access. In the context of cardholder data, encryption drastically reduces the risk of data theft and compromise.
How PCI-DSS standards enforce encryption
The PCI-DSS standards enforce encryption by outlining specific requirements for the encryption of stored cardholder data and the encryption of cardholder data over open, public networks. They stipulate the use of strong cryptography and security protocols to safeguard sensitive cardholder data during transmission over networks that are easy to compromise.
The encryption requirements in PCI-DSS
PCI-DSS prescribes several encryption-related requirements. For instance, requirement 3 mandates that stored cardholder data must be protected through methods like encryption, tokenization, or masking. Meanwhile, requirement 4 stipulates that strong cryptography should be used to safeguard cardholder data during transmission across open, public networks.
Encryption Standards Highlighted by PCI-DSS
Types of encryption highlighted in PCI-DSS
PCI-DSS underscores the use of strong encryption mechanisms to protect cardholder data. It recognizes the use of both symmetric and asymmetric encryption. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses two keys: a public key for encryption and a private key for decryption.
Understanding symmetric and asymmetric encryption within the PCI-DSS context
In the context of PCI-DSS, symmetric encryption often comes into play when storing sensitive cardholder data. Since the data source and destination are typically in a controlled and protected environment, the use of one key for both encryption and decryption does not pose a substantial risk.
Asymmetric encryption is commonly used during data transmission over insecure networks. The use of two keys tackles the risk associated with key compromise in asymmetric encryption. If a cybercriminal compromises the encryption key, they cannot decrypt the data because the decryption key is different and held in a secure location.
Examples of encryption algorithms recommended by PCI-DSS
PCI-DSS recommends several encryption algorithms known for their robustness and difficulty to crack. Examples include Triple-DES (3DES), Advanced Encryption Standard (AES), and RSA. These algorithms meet the PCI-DSS definition of ‘strong cryptography,’ ensuring secure cardholder data storage and transmission.
Applicability of PCI-DSS Encryption Standards
Entities required to comply with PCI-DSS encryption
Any entity involved in the handling, processing, transmission, or storage of cardholder data is required to comply with PCI-DSS encryption standards. Primarily, this includes merchants, payment gateways, service providers, payment processors, and any other entities that store, process, or transmit cardholder data.
Scenarios where PCI-DSS encryption is applied
PCI-DSS encryption is applicable in various scenarios involving the transmission or storage of cardholder data. When transmitting data across open, public networks, businesses must employ strong encryption to protect the data from interception. In the case of data storage, businesses must use encryption to render the data unreadable, thus safeguarding it against unauthorized access.
Understanding the Encryption Key Management Process
Role of keys in encryption
In encryption, keys play a crucial role as they are used to convert plaintext data into ciphertext and vice versa. The strength and security of an encryption process primarily depend on key management, which includes the secure generation, storage, distribution, and disposal of encryption keys.
Key management processes as stipulated by PCI-DSS
PCI-DSS outlines several requirements related to secure key management. It mandates the generation of strong encryption keys, secure cryptographic key operations, and periodic key replacement. Furthermore, under PCI-DSS, old keys can only be used for decryption purposes. Auditable processes for key management are also required to track and monitor access to encryption keys.
Penetration Testing as Part of PCI-DSS
Role of penetration testing in securing cardholder data
Penetration testing plays an instrumental role in securing cardholder data. It is a proactive measure that involves testing a computer system, network, or application to identify vulnerabilities that an attacker could exploit. Within the PCI-DSS context, penetration testing helps validate the effectiveness of the controls in place to protect cardholder data, providing an extra layer of security.
How PCI-DSS guidelines address penetration testing
PCI-DSS provides guidelines around penetration testing and the frequency at which it must take place. It requires businesses to maintain a penetration testing methodology that includes the testing of network infrastructure and applications, review of segmentation controls, and validation of any mitigating controls in place. Furthermore, it necessitates penetration testing after any significant changes to the cardholder data environment.
Importance of regular penetration testing under PCI-DSS
Regular penetration testing is vital under PCI-DSS to ensure continued security. Cyber threats are continually evolving, and new vulnerabilities can emerge over time. Regular security testing enables entities to stay a step ahead of potential attackers, identify any new vulnerabilities promptly, and take adequate remediation measures.
Impact of Non-compliance with PCI-DSS Encryption Standards
Common non-compliance issues
Common PCI-DSS non-compliance issues revolve around failure to maintain a secure network, inadequately protecting stored and transmitted cardholder data, lacking vulnerability management programs, and not carrying out regular penetration testing. Other issues include improper key management procedures, storing prohibited data such as sensitive authentication data, and the lack of a formal information security policy.
Potential consequences of non-compliance
Non-compliance with PCI-DSS encryption standards carries significant consequences. These include penalties and fines, increased transaction fees, the potential loss of the ability to accept card payments, reputational damage, and potential legal action in the event of a data breach. In severe cases, card brands may revoke the ability for an offending business to process card transactions.
Case studies of data breaches due to non-compliance with PCI-DSS
Several case studies highlight the damaging consequences of non-compliance with PCI-DSS. Major breaches typically result from inadequate encryption standards or the lack of an encryption protocol altogether, which exposes cardholder data to cybercriminals. Such security incidents not only lead to financial penalties but also significant reputational damage and loss of customer trust.
Strategies for Ensuring Compliance with PCI-DSS Encryption
Best practices for maintaining PCI-DSS encryption
To maintain compliance with PCI-DSS encryption standards, businesses can adopt several best practices. These include staying updated with PCI-DSS encryption standards, regularly testing and updating security systems, implementing a robust key management process, and encrypting cardholder data both in storage and during transmission. Regular penetration testing and employee training on the importance of data security can further bolster security operations.
Incorporating PCI-DSS standards into organizational culture
Incorporating PCI-DSS standards into organizational culture begins with creating a sense of shared responsibility towards data security. This involves establishing a comprehensive information security policy and ensuring all employees are aware of their role in protecting cardholder data. Regular training and updates on PCI-DSS requirements can also help engrain these standards into the organizational culture.
Tools available for safeguarding cardholder data
Various tools can aid in safeguarding cardholder data and maintaining compliance with PCI-DSS. These include encryption tools for secure data storage and transmission, firewalls and anti-virus software for network security, intrusion detection systems for identifying potential threats, and vulnerability scanning tools for regular system testing. Managed security services can also offer specialized expertise in managing PCI-DSS compliance.
Future of PCI-DSS and Encryption
Emerging encryption technologies and PCI-DSS adaptability
As technology evolves, so do the methods of encryption. Quantum computing, for instance, promises to revolutionize the future encryption landscape. As these emerging technologies become mainstream, the PCI-DSS framework will need to adapt accordingly to ensure the ongoing protection of cardholder data against increasingly sophisticated cyber threats.
Anticipated changes to the role of PCI-DSS in cardholder data encryption
While it is difficult to predict specific changes, the escalating threat landscape suggests that the role of PCI-DSS in cardholder data encryption will become even more critical. Advancements in encryption technologies are likely to be incorporated into the PCI-DSS framework to ensure it stays relevant and robust against evolving threats.
Impact of AI and machine learning on PCI-DSS and data security
Artificial Intelligence (AI) and machine learning have immense potential to redefine data security. These technologies can be leveraged for identifying patterns and anomalies that indicate fraudulent activities, predicting potential vulnerabilities, and promptly responding to threats. Consequently, the future might see PCI-DSS incorporating AI and machine learning within its guidelines to further bolster the security of cardholder data and ensure compliance.