Unveiling the intricate workings of remote access within the cardholder data environment may appear as daunting as it is complex, especially in the context of Payment Card Industry Data Security Standard (PCI-DSS). However, clarity is within reach. In “Understanding Remote Access in the Cardholder Data Environment: A Look at PCI-DSS”, you are guided through the labyrinth of terminologies and strategies designed by PCI-DSS to manage and ensure secure remote access to critical cardholder information. You will gain insight into not just its mechanics, but how PCI-DSS effectively addresses potential intrusions, establishing a strong bulwark against breaches in the sensitive data ecosystem. Stall no further, as we demystify this essential aspect of secure financial transactions.
Understanding PCI-DSS
In the realm of digital transactions, data safety is paramount. One critical standard of this security is the Payment Card Industry Data Security Standard (PCI-DSS).
Basics about PCI-DSS
PCI-DSS is a comprehensive set of guidelines established to govern how entities handle cardholder data, ensuring its security, processing, storage, and transmission. The PCI Security Standards Council, supported by top payment card brands, set these standards. They apply to all entities that handle cardholder data, such as merchants and service providers.
Why PCI-DSS is essential
The importance of PCI-DSS cannot be overstated. It represents a common shared ground to protect sensitive payment card data, ensuring the integrity and confidence of electronic transactions, avoiding potential data breaches, and preserving brand reputation. Non-compliance may result in severe implications, including fines, reputational damage, and loss of the ability to process card transactions.
Components of PCI-DSS
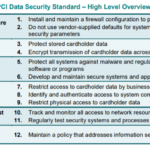
PCI-DSS consists of six major objectives divided into 12 detailed requirements. Those include building and maintaining a secure network, protecting cardholder data, maintaining a vulnerability management program, implementing robust access control measures, regularly monitoring and testing networks, and maintaining an information security policy.
Highlights on Remote Access
The digital age has made almost everything possible from a distance, including accessing data from remote locations.
Defining remote access
Remote access enables individuals or systems to access a specific network or computer from a different, off-site location. It leverages the internet or other network technology, enabling employees to work from various locations while accessing essential resources securely.
Importance of remote access
Remote access has a number of benefits, including boosting productivity, offering flexibility, lowering business costs, improving workflows, and enabling responsive customer service. Moreover, with the rapid rise of remote work, remote access has become indispensable to continue business operations.
Security Challenges associated with remote access
Despite its advantages, remote access also poses significant security risks. Unauthorized access, insecure endpoints, unencrypted connections, malware attacks, and credential theft are amongst the challenges that need to be addressed to ensure safe remote access.
The Role of PCI-DSS in Remote Access
As organizations increasingly rely on remote access, it’s crucial to ensure their operations align with the PCI-DSS guidelines.
Why PCI-DSS is crucial for remote access
As remote access requires transferring sensitive data via the internet, it becomes a high-target area for cybercriminals. PCI-DSS provides a set of practices for protecting cardholder data during remote access and reducing the risk associated with data breaches.
How PCI-DSS improves remote access security
PCI-DSS contributes to remote access security by stipulating required protocols and controls, including strong encryption, secure systems and applications, anti-virus mechanisms, and intrusion detection. It also addresses the need to authenticate users before granting access and regulating access rights according to business role and needs.
PCI-DSS Requirements for Remote Access
Understanding and implementing the right requirements is critical for aligning remote access with PCI-DSS guidelines.
Understanding the different requirements
For remote access, key PCI-DSS requirements include the duty to shield the cardholder data with a secure network, implement strong access controls, and maintain an information security policy. Adhering to these requirements ensures that sensitive data remains safeguarded during remote transmission and storage.
Implementing the PCI-DSS requirements for remote access
Implementation starts with understanding where your organization stands concerning the PCI-DSS requirements. Careful identification and documentation of system components involved in remote access is needed. Steps are then taken to ensure systems and networks are adequately secured, including regular testing and monitoring.
In-depth Look at PCI-DSS Protocols for Remote Access
The implementation’s success rides on understanding the protocols that make it work.
Overview of different protocols
Several protocols regulate the secure transmission of cardholder data during remote access. They include protocols like the Secure Sockets Layer (SSL), Transport Layer Security (TLS), Internet Protocol Security (IPsec), and Secure Shell (SSH), which provide layers of safety for cardholder data during reservations.
How different protocols ensure data security in remote access
These protocols encrypt data being transmitted, preventing unauthorized access. The encryption converts the data into a format that is unreadable by anyone without a specific cryptographic key used for decoding it. This makes it secure during transmission, deterring any potential data breaches.
Case Study on Breach due to Weak Remote Access Controls
An understanding of the potential consequences of weak remote access controls can drive organizations to adopt stringent security measures.
Understanding the impact of weak remote access controls
Weak remote access controls can be detrimental to an organization and its stakeholders, leading to data breaches, unauthorized data manipulation, and financial losses. The repercussions can include significant fines, loss of customer trust, and a damaged reputation.
Lessons learnt from the case study
Such incidents underline the criticality of robust remote access controls and stringent adherence to PCI-DSS. They highlight the importance of encryption, authentication, regular system testing, and vigilance to detect and respond to anomalous activities in the system.
Best Practices to follow in Remote Access according to PCI-DSS
While PCI-DSS provides a legitimate roadmap, some best practices enhance your remote access security further.
Practices to improve remote access security
These include using multi-factor authentication for remote logins, maintaining updated anti-virus software, use of firewalls, timely patching and updating of systems, continuous monitoring and logging of network traffic, and restricting access on a business necessity basis.
Implementing these best practices
Implementation should be systematic, starting with a comprehensive understanding of the existing data environment, identifying vulnerabilities, and remedial action plan development. Regular audits and training of employees about the importance of data security and relevant practices can have long-lasting positive impacts.
Common Pitfalls in Implementing PCI-DSS for Remote Access
With the objective of comprehensive data security, it is prudent to understand potential implementation pitfalls.
Common mistakes organizations make
Some common oversights include assuming that compliance equals security, considering only a part of the system for compliance, failing to keep up with changes in the system, and becoming complacent after achieving initial compliance.
Tips to avoid these mistakes
Stay informed and updated about any changes in PCI-DSS requirements. Constantly educate your team about the importance of data security. Maintain regular monitoring and conduct frequent security audits to ensure continuous compliance. Be aware that security is an ongoing process, rather than a one-time achievement.
Future of Remote Access Security and Role of PCI-DSS
As technology evolves, so will the threats to security. Hence, it’s important to anticipate the future of remote access security.
Emerging trends in remote access security
Trends shape the future, including the increasing use of cloud-based services, machine learning and AI for detecting security threats, increased usage of VPNs, and the rise of biometric authentication – all of these call for an evolved approach towards remote access security.
How PCI-DSS will evolve to meet the changing landscape
The PCI Security Standards Council is committed to evolving the PCI-DSS according to changing threats and requirements. Their responsibility is to ensure that the standard remains relevant and effective in safeguarding cardholder data in an evolving digital environment.
Conclusion on Remote Access in the Cardholder Data Environment and PCI-DSS
Technology and its increasing usage have expanded the avenues of data exposure, making the role of security standards like PCI-DSS crucial in ensuring data protection.
Recap of key points
Remote access, with its convenience factor, does not come without its share of security challenges. PCI-DSS acts as a strong line of defense, providing requirements and standards for protecting cardholder data. Adherence to its principles not only ensures compliance but significantly enhances the security of remote access.
Closing thoughts on the topic
Every organization that manages cardholder data has an inherent responsibility to safeguard it. Embracing and implementing PCI-DSS for secure remote access reflects an organization’s commitment to handling sensitive information responsibly and protecting its stakeholders from the risk of breaches. Remember that security is not a one-time event but a continuous process. It demands consistent attention, regular assessments, and refinement to stay ahead of potential threats.